Computer Networks - Computer Networks Section 3
Consider a network with 6 routers R1 to R6 connected
with links having weights as shown in the following
diagram.
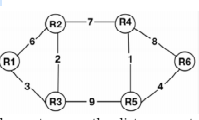
- Option : C
- Explanation : Following will be distance vectors of all nodes.
Shortest Distances from R1 to other nodes (i.e. R2, R3, R4, R5, R6) is represented by vector R1(5, 3, 12, 12, 16).
Used links are R1 – R3, R3 – R2, R2 – R4, R3 – R5, R5 – R6
Shortest Distances from R2 to other nodes (i.e. R3, R4, R5, R6) is R2(2, 7, 8, 12) used links are R2 – R3, R2 – R4, R4 – R5, R5 – R6.
Shortest Distances from R3 to other nodes (i.e. R4, R5, R6) is R3(9, 9, 13) used links are R3 – R2, R2 – R4, R3 – R5, R5 – R6
Shortest Distances from R4 to R5 and R6 is R4(1, 5) used links are R4 – R5, R5 – R6
Shortest Distance from R5 to R6 is R5(4)
Used links are R5 – R6
If we mark, all the used links one by one, we can see that following links are never used.
R1 – R2
R4 – R6
Consider a network with 6 routers R1 to R6 connected
with links having weights as shown in the following
diagram.

Consider a network with five nodes, N1 to N5, as
shown as below.
Consider a network with 6 routers R1 to R6 connected
with links having weights as shown in the following
diagram.
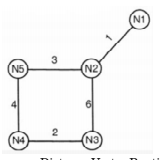
The network uses a Distance Vector Routing protocol. Once the routes have been stabilized, the distance vectors at different nodes are as follows.
N1 : (0, 1, 7, 8, 4)
N2 : (1, 0, 6, 7, 3)
N3 : (7, 6, 0, 2, 6)
N4 : (8, 7, 2, 0, 4)
N5 : (4, 3, 6, 4, 0)
Each distance vector is the distance of the best known path at that instance to nodes, N1 to N5, where the distance to itself is 0. Also, all links are symmetric and the cost is identical in both directions. In each round, all nodes exchange their distance vectors with their respective neighbors. Then all nodes update their distance vectors. In between two rounds, any change in cost of a link will cause the two incident nodes to change only that entry in their distance vectors.
- Option : A
- Explanation : In the next round, every node will send and
receive distance vectors to and from neighbors,
and update its distance vector.
N3 will receive (1, 0, 2, 7, 3) from N2 and it will update distances to N1 and N5 as 3 and 5 respectively.
Consider a network with five nodes, N1 to N5, as
shown as below.
Consider a network with 6 routers R1 to R6 connected
with links having weights as shown in the following
diagram.

The network uses a Distance Vector Routing protocol. Once the routes have been stabilized, the distance vectors at different nodes are as follows.
N1 : (0, 1, 7, 8, 4)
N2 : (1, 0, 6, 7, 3)
N3 : (7, 6, 0, 2, 6)
N4 : (8, 7, 2, 0, 4)
N5 : (4, 3, 6, 4, 0)
Each distance vector is the distance of the best known path at that instance to nodes, N1 to N5, where the distance to itself is 0. Also, all links are symmetric and the cost is identical in both directions. In each round, all nodes exchange their distance vectors with their respective neighbors. Then all nodes update their distance vectors. In between two rounds, any change in cost of a link will cause the two incident nodes to change only that entry in their distance vectors.
- Option : C
- Explanation : In the next round, N3 will receive distance from N2 to N1 as infinite. It will receive distance from N4 to N1 as 8. So it will update distance to N1 as 8 + 2 = 10.


